A newly released report has found that there were 212 ransomware incidents against the food and agricultural sector in 2024. These attacks largely targeted sectors defined as critical manufacturing and commercial facilities and showed a slight increase (0.3 percentage points) in volume compared with 2023.
The data was compiled by the Food and Agriculture-Information Sharing and Analysis Center (Food and Ag-ISAC), which provides threat intelligence, analysis, and effective security practices that help food and agriculture companies detect attacks, respond to incidents, and share so they can better protect themselves. The 212 food and ag incidents were a subset of nearly 3,500 total ransomware attacks identified across 11 key industries in 2024.
“Ransomware attacks are spread out across all critical infrastructure sectors, and specific ransomware groups show a level of variability in their targeting,” the Food and Ag-ISAC said in its report. “While some companies might be specifically targeted, our research indicates that ransomware attacks are typically opportunistic.”
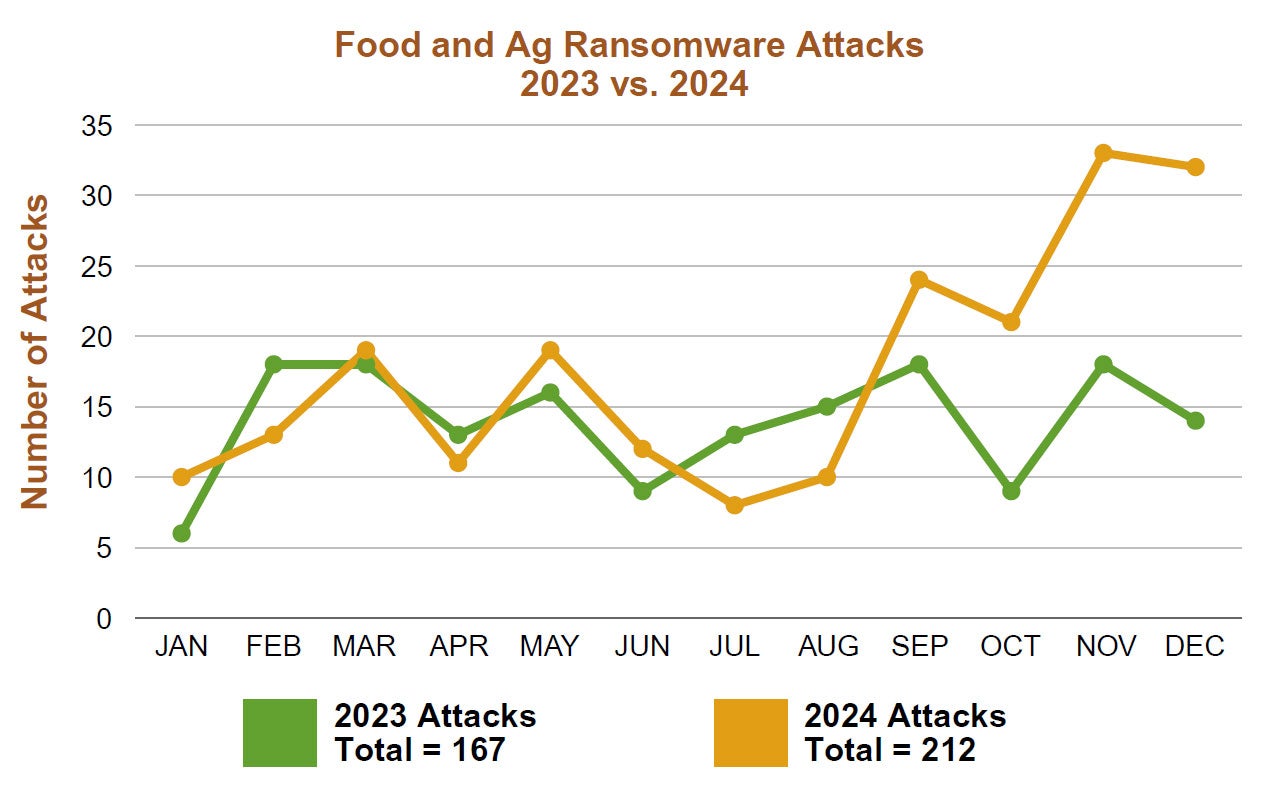
Despite the frequent threat of ransomware and other kinds of cyberattacks, the organization’s report — formally titled, Farm-to-Table Ransomware Realities: Exploring the 2024 Ransomware Landscape and Insights for 2025 — noted that the food and ag sector received fewer attacks than other critical sectors.
One of the most notable of 2024’s attacks was against Duvel Moortgat, which caused the brewery to shut down four Belgian plants and a U.S. facility. Operations resumed within days, but criminals released a terabyte of sensitive data after the company refused to pay a ransom.
Among the most aggressive “bad actors” — the term that is often used in the industry in place of the more popular “hackers” — last year was RansomHub, which has quickly gained prominence because of its ability to recruit affiliates through an attractive profit-sharing model where it offers a 90%/10% split of ransom payments (most offer only 70% or 80%). RansomHub typically targets larger organizations from which they can elicit bigger ransom payments. The group has been spotted using spear-phishing voice scams and compromised VPN accounts to infiltrate target networks.
Another bad actor gaining prominence has been Akira, which uses “double extortion” tactics to convince victims to pay their ransom demands. Double extortion tactics involve infecting the target with ransomware, exfiltrating sensitive information, and then threatening to sell the information unless a ransom is paid. Interestingly, researchers have noted that the group has begun ransomware negotiations with unconventional ransom demands of hundreds of millions of dollars. The group is known to exploit vulnerable, public-facing systems and to target known vulnerabilities in Virtual Private Networks (VPNs), especially those lacking multi-factor authentication.
“As ransomware attacks continue to increase year over year, it’s important for the companies who feed the world to take this issue seriously and prepare,” said Jonathan Braley, Director of the Food and Ag-ISAC. “We strongly encourage organizations to implement multi-factor authentication, network segmentation, regular system updates, and end-user training to reduce vulnerabilities and protect themselves from threats. While the threat landscape is always changing, the Food and Ag sector has met this challenge by working together to share intelligence and collaborate this past year, making it much more capable of responding to these attacks and protecting our networks.”
Other key threat entities are Black Basta, ALPHV/BlackCat, LockBit 3.0, Play, and Hunters International. Any of these actors can have consequences for the victim company’s suppliers or partners and a direct impact on the company itself. In the highly interconnected food and ag industry, a disruption in one company has the potential to trigger cascading impacts.
The Food and Ag-ISAC does offer several suggestions for businesses and individuals to protect themselves:
What you can do to protect yourself from cyberthreats
The following steps should help most enterprises defend against ransomware attacks and help organizations recover if an attack does occur.
Update! Update! Update!: Much like armies look for vulnerabilities in opposing forces, attackers look for vulnerabilities in a target’s network. It is common for vendors to issue “patches” or updates to plug vulnerabilities in their hardware or software as they are discovered. Regularly updating your software can help protect your data and devices from threats.
Be Unique (Stay Weird) with Passwords or Better Yet, Passphrases: Reusing the same password(s) for multiple accounts can jeopardize all accounts, even if only one account is compromised. The National Institute of Standards and Technology (NIST) recommends that unique passwords contain a combination of at least eight letters, numbers, and special characters. Another option is passphrases, which are made up of multiple words, numbers, and special characters — making it longer and more complex than passwords.
Add an Extra Layer of Protection with Multi-Factor Authentication (MFA): Using MFA increases your security by providing additional hurdles to bad actors, requiring two or more distinct types of identification before granting access. MFA works by requesting something you have (phone) with something you know.
Don’t Forget to Backup Your Files (and do it often!): If you were to be a victim of a ransomware attack, you would want to recover as quickly and efficiently as possible. Having a backup of your files and data that you can restore will help you to continue operations as you respond to the incident.
Encrypt Sensitive Files: Remember not all information is equal. Some of your information is more important or sensitive than others. Deploy encryption to protect your most sensitive information and documents, including customer information, Personally Identifiable Information (PII), and emails.
Keep it Separate — Segment Your Networks: Ensuring your networks are segmented will limit and minimize operational risk should there be disruption. To the extent possible, limit internet connections to your operational technologies. If they must be connected, ensure operational networks such as manufacturing and production are segmented from business networks.
Don’t Take the Bait: Phishing remains one of the most common initial access points for cyberattacks, including ransomware attacks. Employees should be trained to avoid common phishing scams.